Truly Hardcoded: TRust-Mobile
Tor-only Rust on Liberux (for browser and universal apps) and Precursor (for hard trusted and dedicated apps)
Why would the So Very Important Powers and Principalities attack a nonperson? Perhaps because everyone is actually potentially someone in the aggregate. The Ruling Quality fears our quantity. Like you probably, I am a nonentity. I won’t presume to make absolute assumptions about my readership, but since reason can be held in common, I can posit certain probabilities just as well as those whose objections I am now anticipating. The latent accusation here is, of course, that as insignificant people we have nothing to hide so we are just being paranoid (and are probably undesirables with damaged brains anyway) if we are concerned about privacy and security matters, even when the absence of these goods is the cause of severe damage to our expendable selves, the selves which we must dutifully sacrifice to the gods of technofeudalism at every opportunity. We are supposedly so without value as the many People—because we are not the few Elites—that it is taken for granted that we do not require personal security and a guarded private sphere because we exist merely a standing reserve to be used up and disposed of at will. Nevertheless, many of us instinctively do not appreciate being mass surveilled, as if it were true that targeted surveillance mechanisms are never abused. Despite what we ought think counter to our self-interests, many of us are aware of a predatory gaze that threatens the biological imperative of self-preservation. Undoubtably, the mass market would really prefer to have private and secure phones if the realm of possible options available in the market was not crafted by our predators.
How Are Civilian Phone Liberties Violated?
Listen to this presentation by Daniel Rigmaiden
Phone Surveillance Terminology
* Base Transciever / Cell Site Simulator
* Masquerade / MIMT
* DRT Inc. - https://drti.com & Key/w —> Third Party Privacy Violations
* LEAP - Local Number Portability Enhanced Analytical Platform
* PenLink & Pin Register
* E911 malicious policing entities cause emergencies to make victims call 911 and then use the E911 data to exploit the victim’s cell phone
→ "pattern of life" is a phrase also used in COIN ( COunter INsurgency )
→ are they hunting for your "bed downs"
So what do you do about it? While I am not fond of the solution proposed by this presenter, namely burner phones—because it is probably just as difficult to obtain an “unknown” phone as a target of surveillance as it is to work towards creating a sufficiently hardened phone or assembling an ensemble of dedicated communications devices—I do appreciate his expression of the futility of all such endeavors considering the results of the following case studies:
* (24:00) CIA/ Abin Omar Case Study
https://en.wikipedia.org/wiki/Abu_Omar_case
* (27:00) the blackbox of the baseband –> why taking the batteries out of most phones is not possible
* (31:00) switches leak RF, SIM rooting
* Bunnie / Snowden Introspection Engine
https://www.tjoe.org/pub/direct-radio-introspection
* IJOP in China – your phone is an ID
https://github.com/hakdogpinas/ptreport/blob/master/Cure53/analysis-report_ijop.pdf
* RF DF (direction finding)
* (1:00:00) Dos / Donts for burner phones
Conclusion? Keep Calm and Stay Paranoid!
Yes, it is reality. You are not just smoking something.
They just want to criminalize your innocent yearning for Freedom.
Tor Browser in GrapheneOS
Now for a technical update. As a journalist who cares about confidential and discrete correspondence, I have been searching for such a safe and private communications device for a while now. In my experience, it is true that Graphene OS is a great advancement
over stock Android and iOS mobile devices. But GOS is not without flaws. For example, I did experience a period of repeated kernel crashes, which has since subsided, but now Tor Browser spontaneously terminates. The browser recommended by the project (Vanadium) is derived from Chromium and is full of improvements beyond the standard Android browser. But Vanadium, contrary to the original development plan outlined in the GOS docs, does not support any transport-layer security in itself beyond DOH (such as the VPN Mozilla or Midori offers, or, ideally, Tor). Do you really trust your mobile ISP with your data? I don’t trust any ISP.
In GOS, Tor Browser can only be run in a “compatibility” mode that disables the default sandboxing features of GOS. I tend to route all my traffic through tor these days, whether on mobile or desktop, since there is not currently—nor is there likely to be—any better design equivalent to the mass user adoption Tor benefits from which makes it the premier anonymity network. Maybe, someday, users of GOS will be able to find a classy, charcoal grey icon of the Tor browser available, a popular app which is as important as Signal, that will exist as an official, validated and sandboxed Graphene app.
Huang’s Precursor
And then I found out about Bunnie Huang’s Precursor mobile device. I knew that the Tor Project was turning to Rust for its memory safety attributes since “half of tracked security vulnerabilities are not possible in Rust” (gitlab.torproject.org/tpo/core/arti). Huang’s Precursor features a Rust kernel, Xous, and is designed to be trusted, meaning that it is possible to verify the integrity of the device software as well as its Open Source hardware through evidence-based procedures. However, the possibilities for apps are not endless on such a Cartesianesquely certain, that is, trusted device. For instance, the convenience of a mobile browser is nowhere to be found. Browsers are too messy to be kept alongside crypto keys that you wish to distribute or secured multifactors which cannot be compromised and exfiltrated. Communications protocols and software like VOIP and an encrypted messenger like Matrix are the only thing keeping the Precursor recognizable as a (Smart) Phone rather than a secure hardware dongle like a Nitrokey or Ledger device.
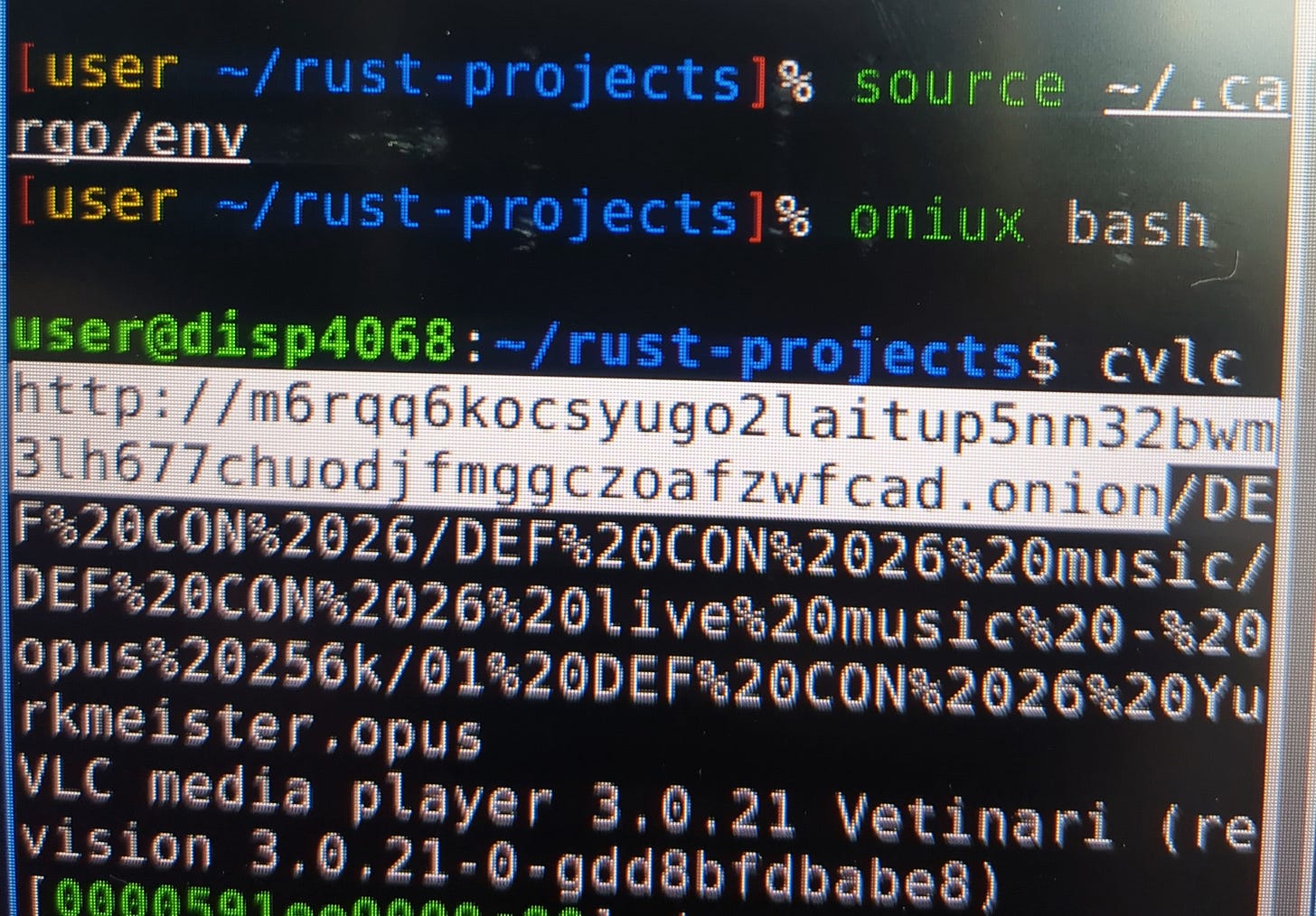
Liberux with Oniux Bash
That is why I am interested in the more extensive and universal mobile computing possibilities that this Madrid based mobile phone company built on Debian Trixie could offer. Oniux bash works great on desktop Linux; why not on mobile Linux as well once all the difficult hardware driver tailoring is ironed out? Take a look at these prompts:
Onionsites can be accessed via an application like VLC or integrated into a messenger like Hexchat. Oniux could then act as the Tor-only gateway for all mobile Linux applications.
IodeOS vs. GOS
If you still can’t do without a mobile browser—and most people absolutely love this convenience or have a dedicated app for every platform / function they enjoy—and if you want a maximally Tor phone, and if Graphene OS doesn’t continue to develop, then there is another mobile OS with microG which can obtain the Tor Browser for Android: Iode OS.
Low Level Functions Now Locked on Android
* (14:51) abd
* (21:00) Lunar OS, Verified Boot, Android Hardening
So why does the foundation of Google ‘s Android code need to be locked? On one hand, there is supposed to be less attack surface to be accessed by exploits, but on the other hand the user cannot scan for viruses with mvt and cannot verify the boot of custom ROMs like GOS on Android 16. In other words, all future generations of the ground-level of Android are not auditable like Precursor’s Open Source hardware and software. Also, Amnesty International’s phone malware scanner mvt can’t access GOS because there is no way to interface through Developer Mode. Is that also true for IodeOS even if its boot can be verified? Testing must continue. . .
Here are Some More Examples of Mobile Spyware Besides Pegasus
Is it a Bug or a Feature: Keyloggers and Rootkits on Mobile
With IodeOS, just say no to Google spy binaries / keylogger with Heliboard, a sponsor of Whonix.
It appears we can now make an educated guess to a question raised earlier in this blog: why did the inventor of PGP, Phil Zimmermann, drop out of developing the Black Phone hardware and focused instead just on the Silent Circle / Signal crypto “middleware” (not too firmware and not too server, just right apps). Answer: probably, he wasn’t Bunnie Huang. Huang had the hardware expertise required to make a trusted hardware platform for a RISC architecture kernel written in Rust with applications also written in memory-safe Rust. That definitely looks like a winning strategy! But, unfortunately, many applications are not suited to this paradigm of hardened trust. Many of the convenient sensor applications and readily available entries into cloud platforms and even the multipurpose browser bring with them too many opportunities for exploits to be kept on the same device as your cryptowallet, multifactor, and messenger. In Huang’s assessment, both the hardware and the software need to be secured and we cannot just rely on good middleware. Perhaps users should disaggregate their devices; the iPhone was a security mistake. Putting everything on the same handsized desktop just wasn’t right for security. Maybe a desktop can take it. A desktop has a bigger processor for stronger math, right? Really, it is not bigger by much these days. No, it seems that physical isolation and having multiple, narrow-purpose dedicated devices is best for security, a principle that is true even for laptop and desktop form factors, which really will just end up being factors of form and not classes of computing power in the future anyway. If you want a mobile browser and Tor, a phone with GrapheneOS, IodeOS, or the Liberux should do the trick. Maybe a secured “cyberdeck” with a browser or media player should be kept for those mobile moments when you aren’t using an encrypted messenger or key distributor. Instead of having just one device for universal apps of convenience, the security paradigm becomes one of dedicating multiple hardwares to particular software. This is a process of concretizing the toolbox of soft programs from out of a Universal Machine and into a variety of immanently hardened and specialized forms: truly hardcoded.