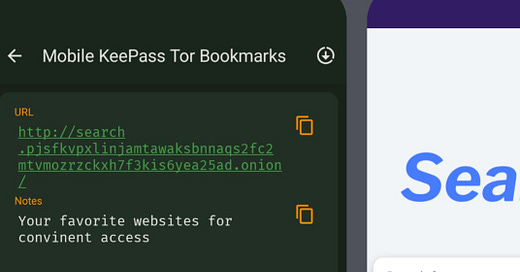
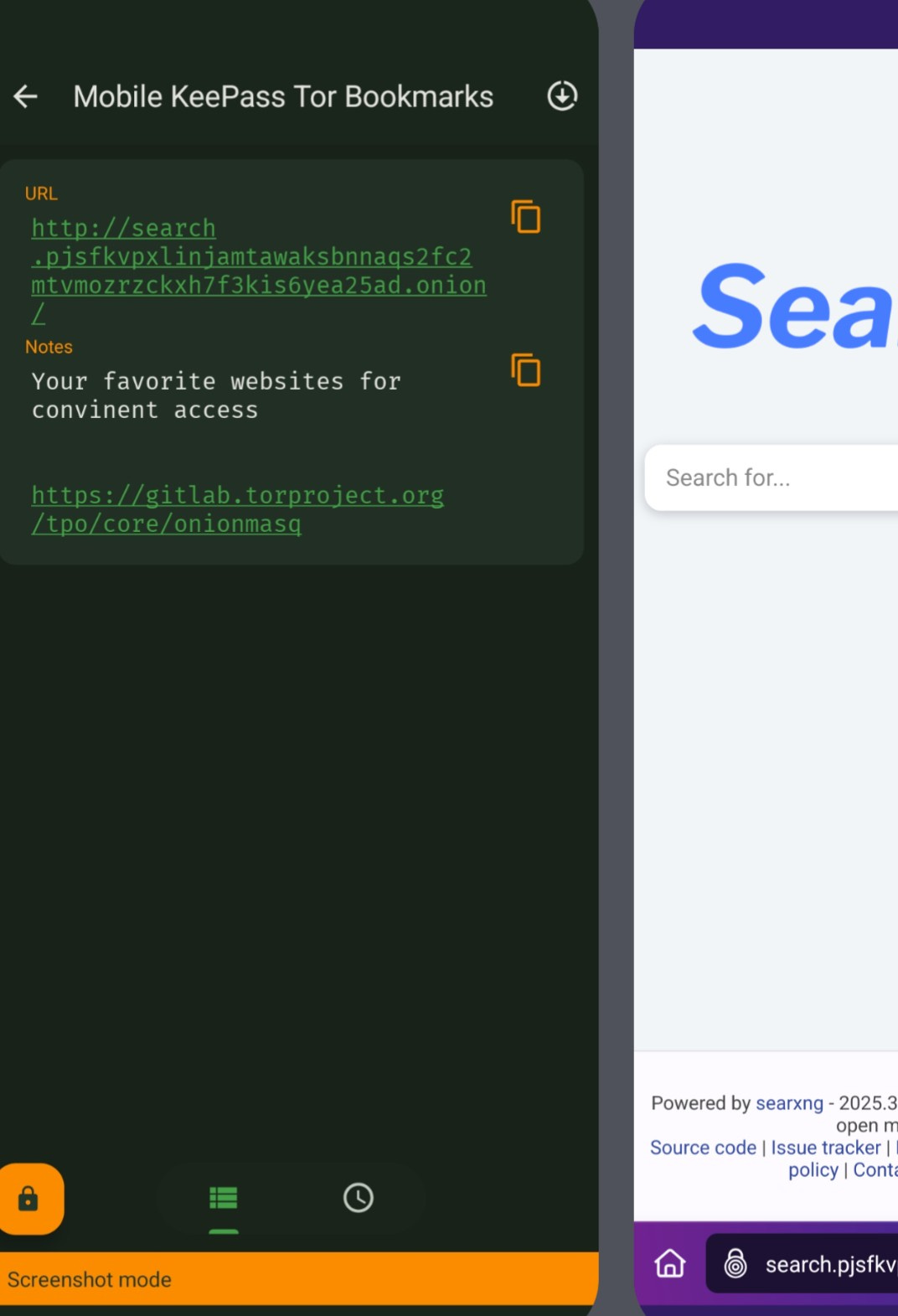
Although capable of accessing onion addresses, Tor Browser for mobile does not provide a prompt to bump up onion-capable sites like the desktop version. While it is not possible to access (parse) bookmarks in the Tor Browser from the vantage of a website, consider that the design of (live) TAILS OS does indicate the potential for OS level probing and forensic imaging of devices connected to—in this case—a private cellular network. That is why I would recommend storing your favorite sites (but not the “top secret” ones, see Inside Story) in an app like KeePass (left, image above) which will open in the default Tor Browser (right, notice concentric onion icon). This makes accessing the sites very convenient. No one wants to type in 56 characters on their cell screens every time they want to read a publication or access their onion webmail. In the future when more web pages utilize onionspray and offer an onion address, this will be a good method to store addresses and access them with just one touch.
There is no reason not to utilize the best available encryption in a free country. However, not all countries follow the same laws and practice the same security customs. The news outlet RFERL is full of stories about the repression of journalists and dissidents.
Law and Order - https://about.rferl.org/article/law-and-order-in-tajikistan/
Death, Detention, Deportation - https://www.rferl.org/a/majlis-podcast-karakalpak-activists-detentions-pannier/32845976.html
Tajikistan’s Descent into Despotism - https://www.rferl.org/a/majlis-podcast-tajikistan-despotism/33324939.html
Clamping Down on Religious Freedom - https://www.rferl.org/a/majlis-podcast-religious-freedom-central-asia/32943016.html
If you are living and working in conditions like these and are facing torture and/or years of imprisonment, the best policy would be to have a smart phone with a browser configured for private browsing that stores no history and sanitizes on shutdown (a version of Firefox is a good candidate). You might regularly delete the phone numbers of people you have called and keep your contacts’ information only in your memory. But it is likely that the authorities would also have access to your the metadata of your cell network if they can have access to your device. You probably would not want to take anything but innocuous pictures and if you stored any information, you would have to make sure it could never be construed to be critical of authorties. If you needed to get a story out, you could store information that would be erased with a panic button like the Graphene’s Duress function, but that might also appear suspicious to some one holding you in custody who then might torture you to make you tell them what you erased. In the US, these precautions should not be necessary. In the US, your device is Constitutionally protected by the 4th Amendment. Software like Cellebrite may be used without your consent but will be inadmissible without a warrant from a judge.
Recently, two US Senators and the DNI exchanged an open correspondence that alerts Americans to the desire of the UK government to undermine the security of Apple Computer’s cloud services. Readers will likely recall a contrasting event involving Apple and National Security interests. The UK is known to be a more oppressive government than the US when it comes to draconian terror and libel laws that make the US Patriot Act look good in theory, if it were not for the fact that the underlying destructive deep state lawlessness that damages hapless civilians in the United States is not really different from that force in the United Kingdom.
Several varieties of actors and motives are active in the world besides Anglo-American National Security interests and our phones are potentially connected to any and many of them. A global perspective on cybersecurity for civil society that acknowledges this state of affairs is expertly taken up and investigated by a University of Toronto internet observatory called Citizen Lab. Ronald Deibert’s new book Chasing Shadows: Cyber Espionage, Subversion, and the Global Fight for Democracy chronicles the efforts of Univeristy of Toronto’s Citizen Lab and their partners to create actionable “counterintelligence for civil society.”
After learning about the various cyber threats that Citizen Lab has sought to mitigate and the stories of people who have been targeted around the world, what might be a few examples of defensive technologies to keep in mind that would serve people facing similar threats? What is the best possible phone we could recommend to the victims of these cyber attacks and people like them?
[See Suggested Reading at end of page for more information.]
The Current State of Mobile Linux
Turns out, most mobile Linux operating systems are nowhere near ready for prime time in today’s highly contested space filled with advanced cyber threats. If you thought a mobile Linux OS would be just like the server and workstation counterparts, you would be mistaken as was I. In the case of mobile device platforming, it appears that the initial interest which brought many Linux Operating Systems to a mature state of development was eventually throttled instead of sustained. A distribution is only as powerful as it’s hardware-specific driver writers and physical, non-abstracted idiosyncratics? Maybe so. Something happened that thwarted efforts to make progress or shut down the mobile projects entirely. Was the competition interrupted and silenced? Was it the burden of COVID?
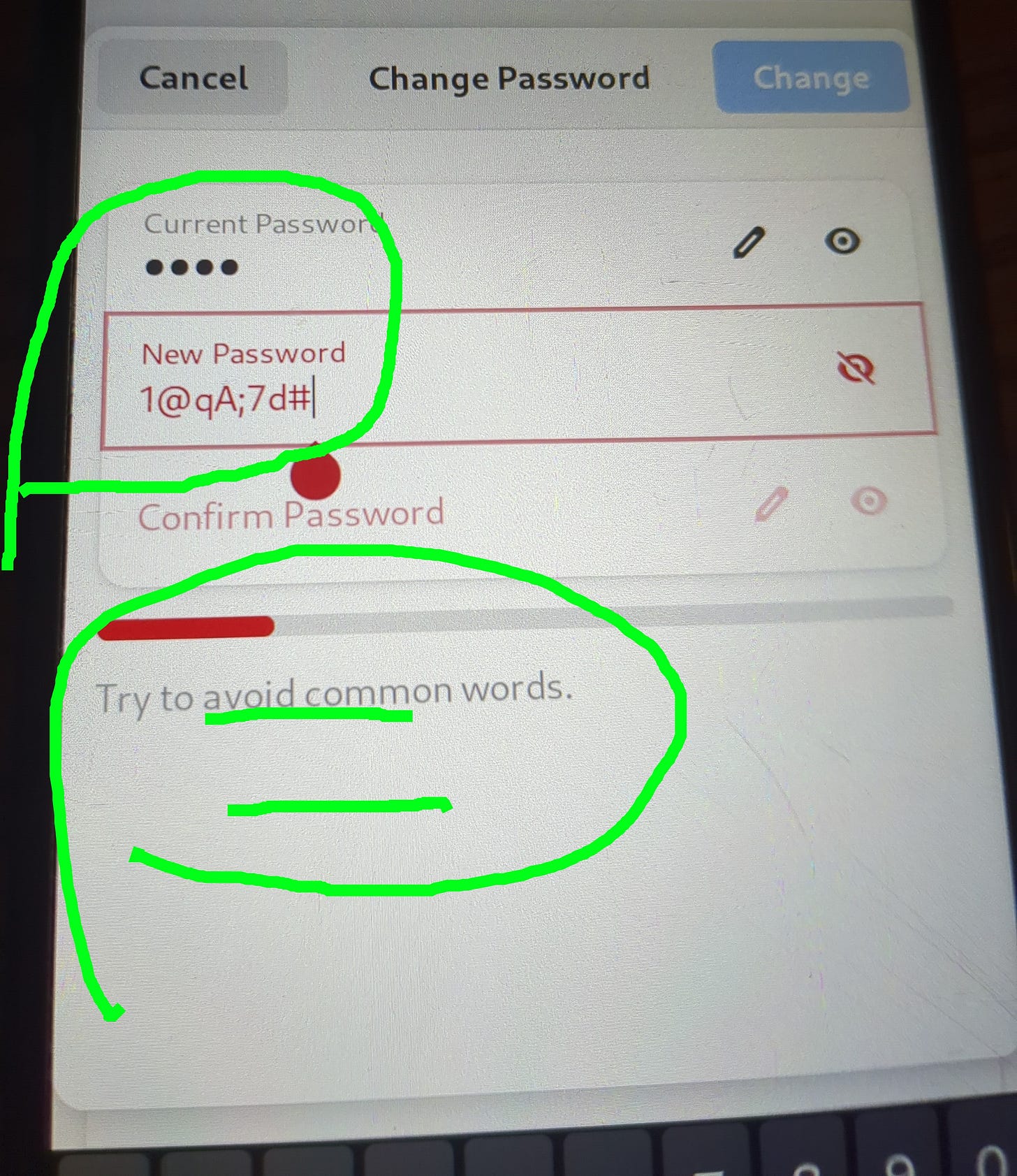
Changing Mobian password
Super user and passwd do not change lock screen on many mobile distros. Either gpg verified sha sums can be forged or Mobian did not allow users to have log10=24 long complex passphrases. If technology is found to be suspect by the user and is not up to their standards of quality, the user will not adopt the the technology.
Does that look like a common word to you? At one time, PostMarket OS pmbootstrap had an --fde (Full Disk Encryption) option but neither the git or apt has been maintained. The .img is available and boots but screens are fragile without tempered glass (see below).
Hardware switches are really nice but that doesn’t stop Quark (all networking hardware removed physically and still there is a TEMPEST capability). Certainly no BT “smell” with a hardware switch. Bluez can be blacklisted on the kernel level and geoclue can be configured to enhance rather than undermine privacy.
After all that, probably better to throw the dough at Jolla until more developers get involved in rejuvenating the mobile Linux ecosystem. Sailfish OS is a robust software company staffed with a team of developers in Finland, a country with a large mobile engineer talent pool and home to phone giant Nokia. If you are looking for a Linux phone that is on par with Graphene OS and is not influenced by Google, try a license from Jolla. All you need is a thirteen hundred dollar Xperia plus shipping costs from the EU which can be difficult to obtain! Hopefully what you get is better than a couple iPhones that would cost just about as much! Another company that is about as pricey but is based in the US is Purism. Costly phones, but probably worth it if you want a secure business network.
Preamble Handshake
The pursuit of secure telecommunications has an entertaining history and the functionality of this technology has greatly increased over the years. If you take into account the technical specifications of today’s iPhones, for example, you might wonder why smart phones should not be able to equal laptops and desktops when it comes to generating and executing the strongest cryptologic functions now available given that they are capable of comparable processing power (not just a Great Firewall lhttp-only browser in the emmc they can use Spectrum Dominance ‘quark’ on).
Books can be written about the subject. After chronicling the story of a phone company that served clients engaging in various dirty deeds, Joseph Cox concludes his recently published book Dark Wire with a discussion about what encrypted phones might mean for non-criminals. The author concedes that take down of criminal enterprises does nothing to end the drug trade. The race against internet security and the war against communications privacy are also futile. This is why, referencing at least one company, Graphene OS, Cox writes that "the impediment to action advances action," meaning that this effort to undermine communications privacy will only contribute to the redoubling of efforts to fortify such an essential human concern.
Additionally, most professional cybersecurity experts will admit that a backdoor for the government is equally a backdoor for bad actors in every system, including the (Pavlovian spy-pager, ankle bracelet) devices that practically everyone in modern society carries with them at all times.
But if you do not want encryption for organized crime, why would you want it for the military or police? Police constantly abuse our civil liberties and act unaccountably in the dark to violate our rights with immunity. It all never needs to get to the judges, they just attack citizens violently and clandestinely, seizing their private data whenever they please. No one is going to see the phone records and internet traffic of the Military Police. Can we plaintext $390+ million police phones? Why not? They must be hiding something.
The Kicksecure Datasheet
Before dividing this article into a few crucial, exploratory technical subsections, the inquisitive reader might appreciate this brief overview of the privacy and security focused phones available on the market today.
Now, apprised of several of the available mobile phones in this class and of their technical characteristics and the goals of their respective developers and software communities, there are a few questions we might ask ourselves before choosing among these options or developing our own phones.
Later, if you haven’t already decided for yourself what phone best meets your needs, you might return to this discussion with a more developed view able to discern for yourself the better from the worse according to your informed judgment. The point is to recognize that there is agency in technology—and it varies—not an absolute, singular arithmetic. Although the uniformity of mass productions and the specialized nature of technical information might present consumer choices as dictated defaults chosen by another instead of elected selections chosen by oneself, it is worthwhile to consider good tech as the aggregate of a series of trade-offs met with discernment.
Mobile Transport Networks
Very interesting interview: Harry Halpin’s Forecast in 2025 (NymTech)
Veilid - https://veilid.com/chat/
Tor Mobile - https://support.torproject.org/tormobile/
Towards Updates Over Tor on Mobile
In my experience, the best way to update Linux devices is with tor and onion repositories. This is because, for instance, updating with http but no encrypted transport, even if it is GPG signed (think verified) as is the case with dnf5, means that an attacker still has access to metadata that can be used to target and attack a victim or obstruct the update. Since it is possible to access tor tor on mobile devices and to access onionsites, why not update phones with tor and onionized repositories? If you don’t think this is possible, just take a few minutes to try out Tor Browser on Android or iOS by downloading the browser from your app store and then simply navigate to Startpage .onion search. It works (if the FEDs haven’t smashed all the sand castles right now)! Then, Mobian OS, derived from Debian which has onionized repositories, should be able to be configured to update over tor from onionized repositories without excessive difficulty (in the future).
We need a lot more tor development on mobile. For more information, check out these links:
Graphene OS can be updated with encrypted private system DNS (tls) and with certain VPNs and proxies but not with tor. GOS apps can be updated over tor with Orbot and Fdroid—even with Accrescent and perhaps with Obtainium—but not with Google Play Store.
At one time, GOS intended Vanadium to proxy with VPN or “tor.” That intention seems to have been removed.
(The Military Police state just wants to intercept all phone traffic with centralized dns (no OpenNIC) so they can learn who has some script and then extra-judicially hellfire them. Scripts are not terrorism! Qubes OS updates over tor. Is it a criminal project just because troopers are Army retards?)
What are the Best Encrypted Messengers?
First, you might ask if network layers and modes matter or if it is all just about the encryption at the application level. If we are to draw any conclusion from the fact that the inventor of PGP, Philip Zimmermann, abandoned the Blackphone hardware project and works only on the Silent Circle app, it must be true that the application layer can make up for insecurities in the network and lower level layers. Or, making the full hardware and software package was too challenging. If you were not even aware that cellular networks come with protocol insecurities like SS7 and vulnerabilities in the baseband radio firmware and are operated by Federal entities, then the question might have appeared moot at first glance. But if there are intractable flaws in the carrier, perhaps our phones could be connected by a network infrastructure we maintain. There are no “local control” cellular LANs. But it is possible to build community owned infrastructure with LoRa (low bandwith but considerable distance) radio towers or use Bluetooth in a close local area. The last option might require verifying that it is really possible to secure the notorious Bluetooth protocol as Briar must claim (it is possible to tor TB and use BT but I would not advise that). However, Briar if fully capable of utilizing tor on cellular or wireless networks even if this app requires real-time communication or a dedicated mailbox device.
Cwcth
Cwcth looks like the best option to me because an individual or organization can build their own onionsite server to relay messages.
Molly
Molly is a fork of Signal that works with tor. Signal is currently the secure messenger standard but is only available on Company app stores and does not utilize metadata protection networking as Molly does with tor (socks5).
The Revolution will not be Signaled?
https://www.counterpunch.org/2025/03/07/the-revolution-will-not-be-signaled/
Briar
Briar is an interesting messaging app that utilizes tor and can communicate locally in case larger scale networks are down or undesirable. The need for an always-on inbox might detract slightly, but if used for real-time event communication, it would be very secure and useful. Couldn't have been shut down in Tahrir Square or Hong Kong's Umbrella Revolution. No reason Bluetooth can't be encrypted and secured like the progression of wireless WPA standards, although it is more easily scanned for than cellular which requires a cell site simulator.
Local Network Infrastructure?
LoRa is also of interest for local communication and can serve as a method to carry encrypted messages.
DIY Hardware and Software Alternatives
Pine 64 – See info at beginning of page. If not an advanced mobile developer and/or team of them, I recommend that you test the Sailfish OS license - https://shop.jolla.com
Mecha Comet - Mecha is a crowd source project to build a mobile linux computer set to debut this spring. One of their project options is a phone, which will require a cellular hat of some variety.
Mecha is recommending Ada Fruit Fona or the 3/4G Pi Talk (sixfab). But since LTE doesn’t always do the trick, there is a n258 5G mm wave but Quectel is on the list and this hat is bulky (even minus casing)
https://www.waveshare.com
Mecha is reminscent of this project, but for phones instead of laptops.
Mobian OS - Debian for mobile. In need of development like almost all of the mobile distributions. FDE should be a priority.
NixOS - Always want to get in to terminal on a phone. There is more than Termux with NixOS and other Linux based mobile phones.
Fedora Touch and Ubuntu
https://discussion.fedoraproject.org/t/how-to-install-fedora-linux-on-android-mobile-devices/85867
https://devices.ubuntu-touch.io/
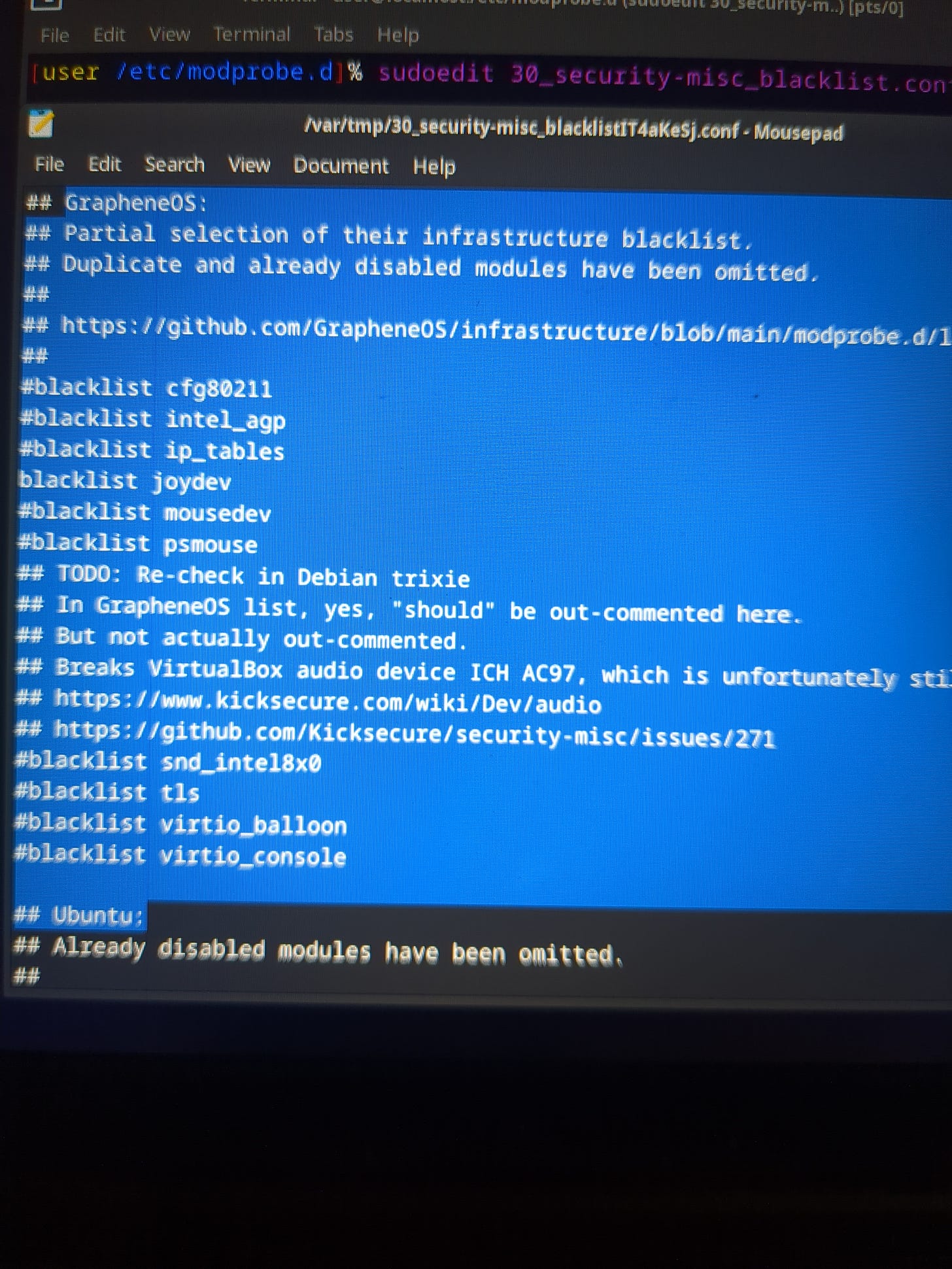
Miscellaneous Security Features
Kernel hardening is important. I guess GOS doesn’t like joydev (joysticks) either. Take a look at this blacklist in Kicksecure (/etc/modprobe.d/30_security misc)
Sandboxing in GOS - https://grapheneos.org/features#improved-sandboxing
Sandbox Firefox browser (Fennec) - https://www.ghacks.net/2017/01/23/how-to-change-firefoxs-sandbox-security-level/
ROMs (.img) and Memory Safety in Mobile Devices
Something to think deeply about. True of mobile devices as with larger platforms. What about a mobile Live mode? GOS has a safe mode.
iOS has a safe mode also - Apple Lockdown Mode (CS 326)
Cloud Qubes
True, some people would point out that self-hosting cloud services in a country like the UK would be worse from a legal perspective and would also require time set aside to maintain the integrity of those technical services. But someday, there might be ways to remotely connect via a phone/handset to cloud services similar to the way Qubes OS proposes.
https://www.qubes-os.org/news/2018/01/22/qubes-air/
Linux Development Environment
Boot Debian via Developer mode on Android.
Suggested reading and links to people and topics of interest in Chasing Shadows
Wyden Schiff NSO Sanctions - https://www.koin.com/news/oregon/sen-wyden-says-oregon-should-divest-from-spyware-company/
House Intelligence Committee to “regulate mercenary spyware” (305)
SS7 (p. 66, 68) - Nils Putnins
DNS cache poisoning - https://www.cloudflare.com/learning/dns/dns-cache-poisoning/
Jamal Khashoggi (81)
Bahr Abdul Razzak - https://citizenlab.ca/people/
Harold Innis - https://www.media-studies.ca/articles/innis.htm
Steven Loleski – https://www.tandfonline.com/doi/full/10.1080/02684527.2018.1532627
Maarten van Horenbeek – malware examined inside VMs
Amnesty International spyware scanner (217) - https://docs.mvt.re/en/latest/
home location register (218)
VPNs can be used to detect exploit traffic vs. the more stealthy “smash and grab” zero days (219), spyware remains elusive (233)
Access Now - https://www.accessnow.org/
Wave guard tracer - https://waveguardtechnologies.com/tracer/
(For a Civil counterintel counterpart to IMSI catchers check out EFF’s Rayhunter —> https://github.com/EFForg/rayhunter)
Fieldwork (261) communicate discretely and keep a low profile
Lex Super Omnia
More links